Recently I’ve been working with several Office 365 customers who are considering Okta or they have already invested in Okta as their primary identity provider (IdP) solution. These customers have been asking questions like:
How does Okta compare to the Microsoft Azure Active Directory (AD) identity solution?
What is the end-user experience if I switch from Okta to Azure AD or vice versa?
What are the advantages or limitations one way or the other?
So, I decided to build out a lab environment with both solutions to gain a firsthand experience. The following diagram represents this lab environment which simulates both an Okta federated domain, PCTGOKTADEV.US and an Azure AD managed domain, PCTGDEV.US.
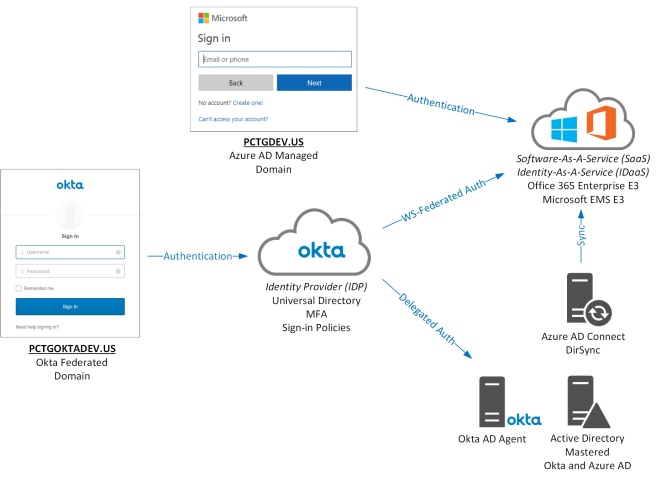
In the video below, we will cover the following Office 365 end-user scenarios for both the Okta federated domain and Azure AD managed domain:
- Initial sign-in to portal
- Trusted sign-in to OWA
- Non-trusted sign-in to OWA
- Outlook profile configuration
- Risky sign-in from Tor browser
- Restricting applications to corporate owned-devices
Hopefully you find this information useful in understanding the difference between the Okta and Azure AD experiences for Office 365 users.
Thanks for tuning in and please comment and let me know if you would like to see other scenarios demonstrated.

